Row Hammer Phenomenon
Row hammering in DRAMs can occur when a specific wordline of a DRAM cell is activated repeatedly within a refresh interval. This is called a Row-Aggressor. In this situation the neighboring cells leak charge at a faster rate than expected. Thus, the retention time of such cells becomes less than refresh cycle (e.g. 64 ms) which means that these cells may lose their data (charge) before the refresh happens (Row-Victims). Therefore, during refreshing process the corrupted data will be read and written back again to the DRAM cell.
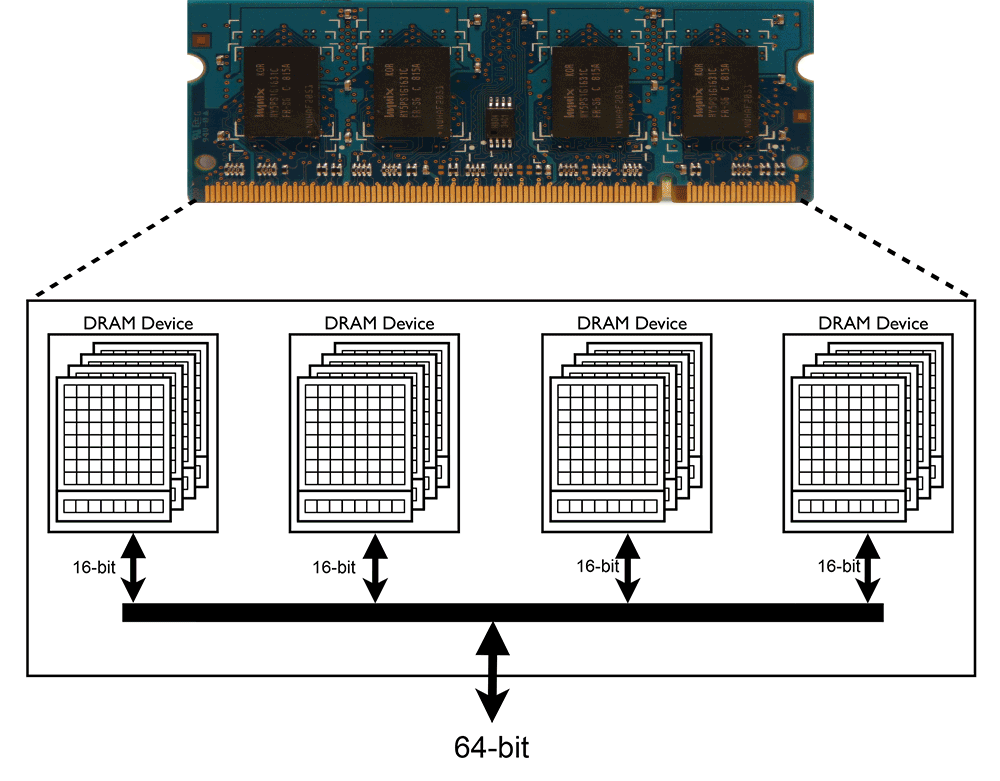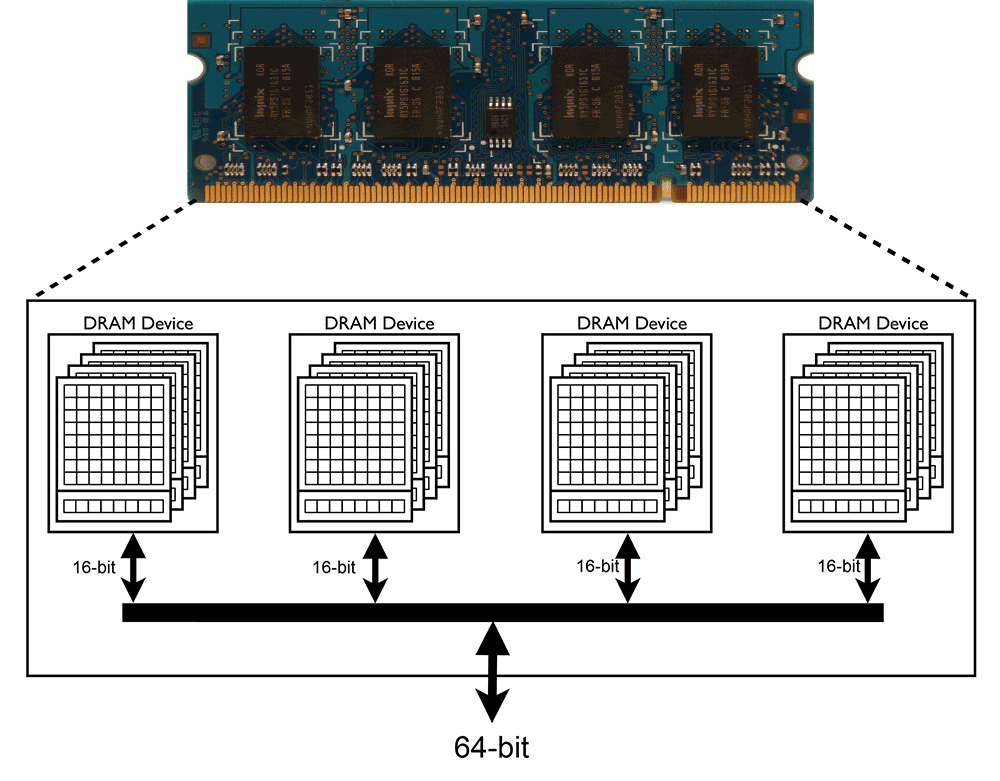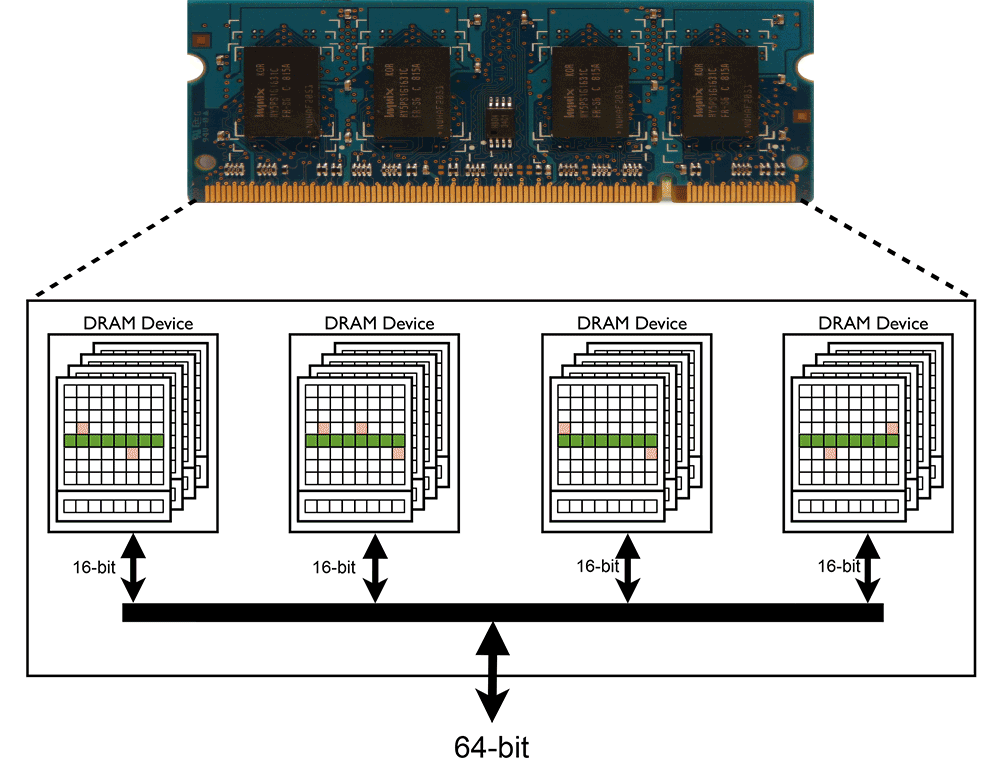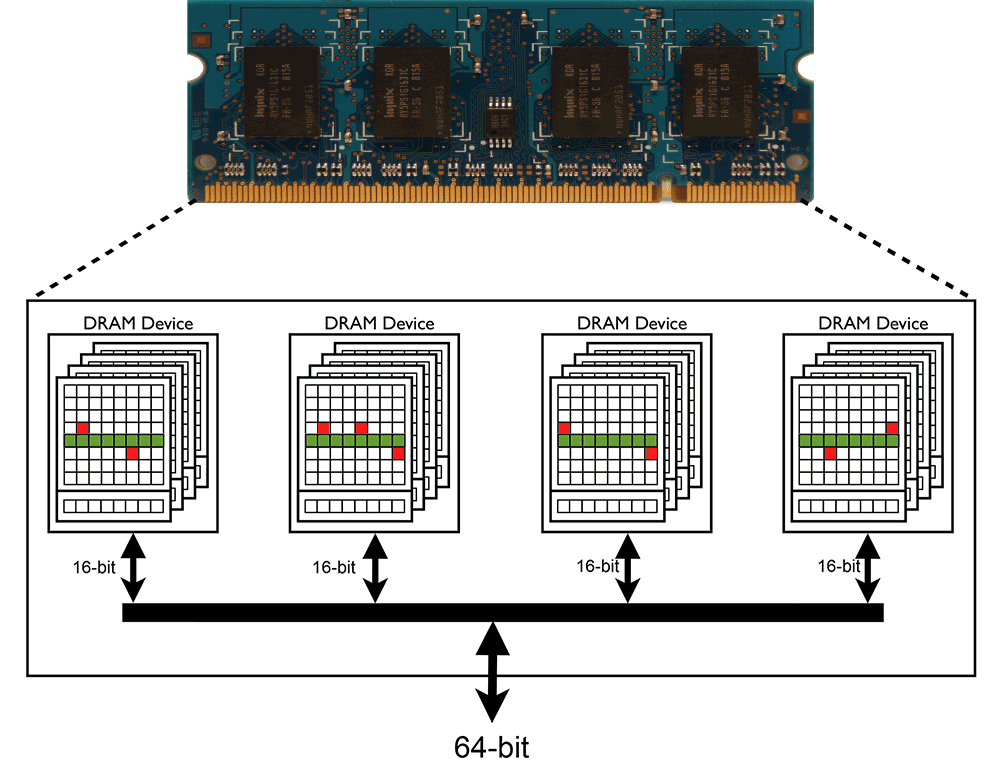
Double-Sided Hammering
The Row Hammer phenomenon can be even more critical if a Victim-Row undergoes hammering by its two adjacent Row-Aggressors. In this situation the victim cells will lose their electric charge even in a faster rate than the single-sided hammering situation.
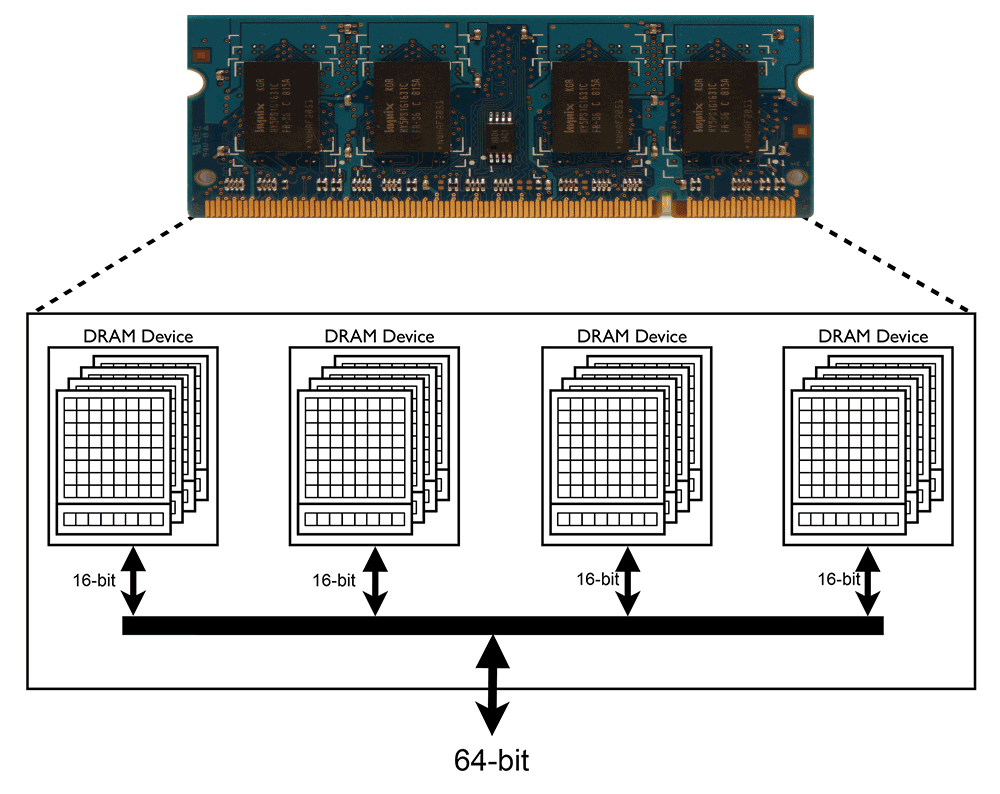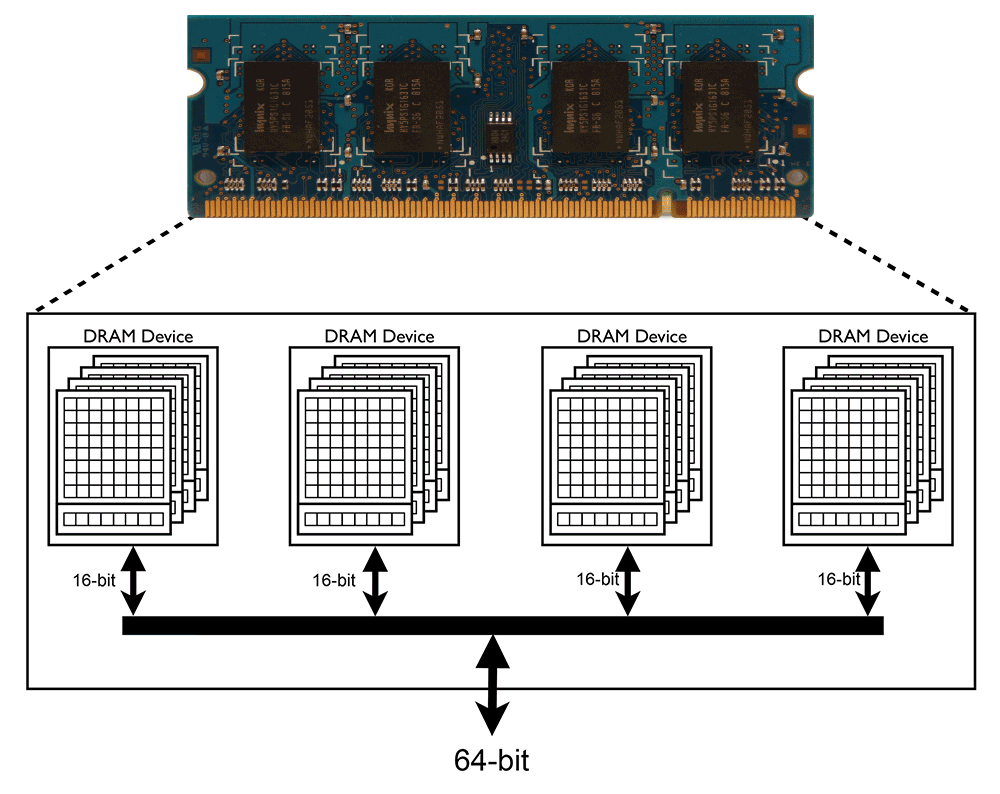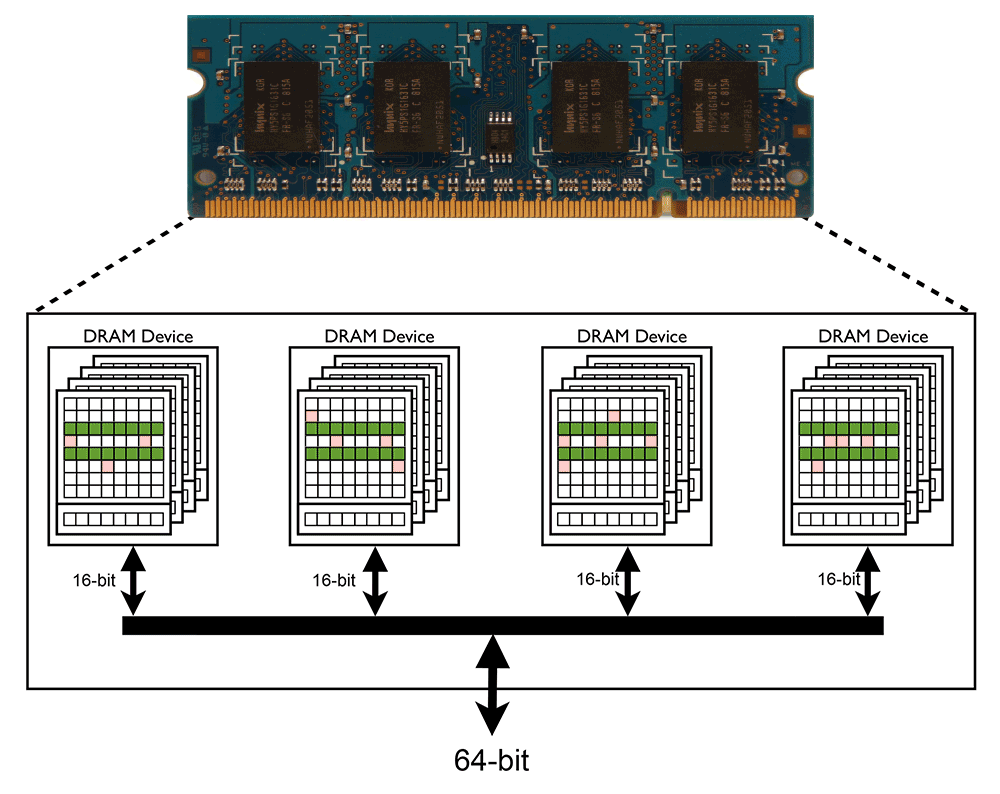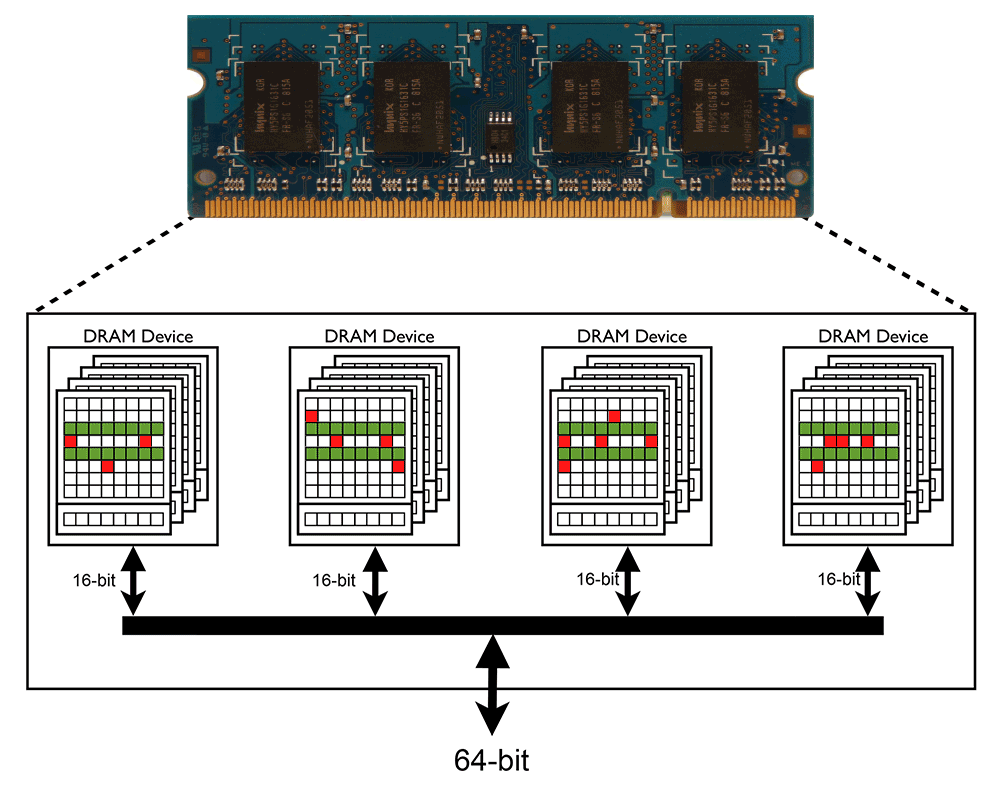
Google - Project Zero
(Exploiting the DRAM Row Hammer Bug to Gain Kernel Privileges)
Google's Project Zero engineers have exploited the vulnerability of DRAMs to Row Hammer error to gain kernel privilege and run unauthorized code. They have also released code that can be run on personal computers to check if the system susceptible to Row-Hammer error. Now the question is how to protect our systems against such a scary error?
Potential Solutions
One straightforward solution to mitigate row-hammer is to simply increase the refresh rate for all the rows in the memory system. Although, this approach might alleviate the Row Hammer error, it imposes an unnecessary power and performance overhead to the system. Probably, the most intuitive solution is to detect the rows with a high number of activations (i.e. ‘hot’ rows) and refresh the adjacent rows. A simple method to recognize hot rows in a DRAM is to dedicate a counter per row to keep track of number of activations of that row. However, having one counter per row induces a significant area and power overhead to the memory system. Researchers at Carnegie Mellon University (CMU) investigated this phenomenon and proposed a probabilistic-based technique (PARA) to mitigate the Row Hammer effect. Although the solution presented by Kim et al. is simple and reduces the probability of Row-Hammer error in DRAMs due the probabilistic nature of the technique it is not the best option when facing the security issue in memory systems.
How We Solve Row Hammer Effect
[1]
[1]
[1] DRAM picture is taken from - http://en.wikipedia.org/wiki/DDR2_SDRAM - CC BY 3.0
School of Computer Science - Advanced Processor Technologies Group (APT)
© 2015 The University of Manchester - All Rights Reserved

